Some Known Details About Disaster Recovery
organization continuity: Know the distinction In the company globe, disaster recovery is often made use of interchangeably with organization connection (BC). While these terms are comparable, there are some essential differences to keep in mind: Business continuity has to do with maintaining a company operational when a disaster strikes Calamity healing concentrates on recovering access to information and also IT framework complying with a physical or virtual incident As an ideal method, you should have maximized company connection and catastrophe recovery strategies in place to keep operations and also recover gain access to after a triggering occasion.
Reputational injury Services are likewise at risk from reputational damages following a prolonged interruption. Individuals today have high expectations as well as expect instant and reliable access to on-line services, 24 hrs a day. When customers can not access on the internet sources, they have unfavorable experiences. Relying on how poor it gets, they might despair in the brand, complain on social networks, and possibly even change over to competitors.
With this in mind, IT calamity recovery typically centers around the complying with tenets. Know what you don't recognize Companies commonly think they have the sources and also techniques they need to effectively recuperate from a calamity.
Getting The Disaster Recovery To Work
Services have a tendency to make the mistake of thinking solution suppliers as well as companions have failproof plans, which leads to complications. It's much safer to form a plan rather of counting on other agencies for organization continuity.

Post-disaster After the disaster ends, staff member need to know when to return to regular workflows and also move off backup systems. As soon as the catastrophe remains in the rear-view mirror, you must continue replication to make certain you are still syncing to backup systems. At the end of the process, it's critical to debrief the goal.

Rumored Buzz on Disaster Recovery
Checking and also analysis As soon as you have a viable catastrophe recovery strategy in place, your service will certainly require to work to examine and update it. By screening and examining your catastrophe healing strategy, you can ensure that it's relevant as well as up to speed up check this with the existing needs of your organization.
The faster you reply to a cyber occurrence, the much less damages it will certainly trigger.
Now, we've all listened find out here now to stories regarding ransomware and also the squashing effect it can have on small companies. Simply like a crook can hold a person captive in exchange for cash, cyberpunks can hold your essential information as well as need repayment. With the current shift to home work, ransomware attacks greater than doubled in 2021.
A Calamity Recovery Strategy is essentially a video game strategy for exactly how to deal with a ransomware assault (or other type of cyber attack), ought to one take place., prevents your business from dealing with disastrous consequences at the hands of a hacker.
Disaster Recovery - An Overview
Your strategy must comprise every division within your company as well as be evaluated to ensure your entire team recognizes exactly how to respond in the event of an unexpected assault. Maintain these ideas in mind when developing a first-rate Catastrophe Healing Strategy: Your strategy needs to consist of each of the following important components: Goals for recuperation that are clear for every division within your organization, As pointed out over, this need to include,, and you will certainly need in the event of a catastrophe.
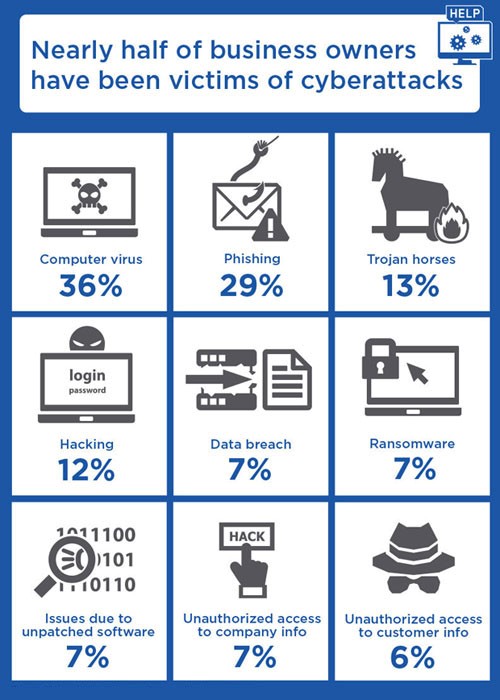
It includes the required procedures, properties, workers and also services. DRPs have actually become a staple in contemporary business. They can play an important duty in maintaining a business going lengthy term when they are created and made use of properly. Every company is unique, yet there is a fundamental theme. Right here are the crucial aspects of a catastrophe recuperation strategy layout as well as why they're necessary.
Preparation is essential when it comes to reducing the impacts of a possible ransomware attack. A Calamity Recuperation Plan is basically a tactical plan for how to deal with a ransomware attack (or other sort of cyber strike), need to one happen. A solid plan, combined with preventative protection solutions, prevents your organization from dealing with catastrophic consequences by a cyberpunk.
The Main Principles Of Disaster Recovery
Your plan must comprise every department within your view company as well as be examined to guarantee your entire group recognizes just how to react in case of an unforeseen strike. Keep these tips in mind when developing a first-class Disaster Recovery Strategy: Your plan needs to consist of each of the adhering to crucial parts: Goals for recuperation that are clear for each division within your organization, As mentioned above, this should include,, and also you will require in case of a calamity.
The secret to restoring your systems promptly is to avoid any kind of confusion and obtain every person on the same web page as early as possible complying with an attack. You should also have a clear understanding of that needs to be contacted in the occasion of a case and also just how they can be reached.
DRPs have actually come to be a staple in modern-day service. Below are the crucial components of a calamity healing plan design template and why they're vital - disaster recovery.